Every few weeks, someone asks me the same question: “What do you actually find in a typical web penetration test?”
Instead of answering anecdotally, I pulled the aggregated data from the last 12 months of web application tests (including APIs) performed by binsec GmbH. The result is the graphic below – and it reflects the same pattern I’ve been seeing for years.
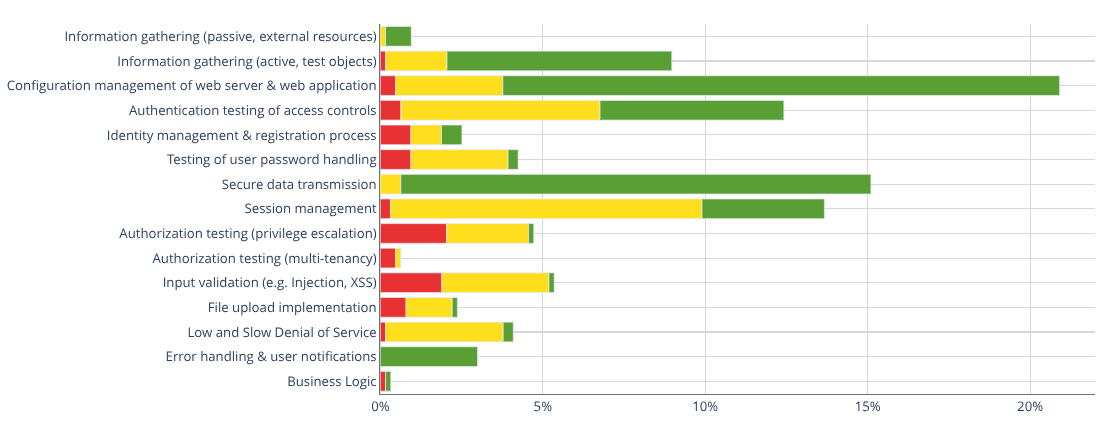
Configuration Mistakes: The Everlasting Low Hanging Fruit
A large proportion of findings originate from simple configuration issues: insecure web server defaults, missing security headers, outdated TLS versions or weak cipher suites. These issues are easy to detect and usually not catastrophic, but they highlight a recurring pattern: deployments often lack a basic security baseline. A single security checklist would prevent most of them.
Session Management: Old Problems in Modern Applications
Session handling issues appear surprisingly often. A typical example is that logging out invalidates the session only in the browser, while the server-side part of the session remains active. If someone compromises the session token, they can continue using it even after the legitimate user has logged out.
Where the Critical Issues Hide: Authorization
The majority of critical findings occur in the area of authorization testing, especially regarding:
- missing object-level access control,
- insufficient role enforcement,
- privilege escalation paths,
- weak tenant isolation in SaaS environments.
Modern, frontend-heavy applications make this problem more visible. Browsers call dozens of API endpoints, and each endpoint requires explicit authorization logic. Frameworks rarely enforce this automatically. Developers have to implement it manually. A manual process that inevitably lead to inconsistencies.
The Classics That Refuse to Die
SQL Injection and Cross-Site Scripting (XSS) are far less common today, but they have not disappeared. ORMs, prepared statements and validation functions prevent many of these issues, but the moment someone bypasses them “just for a quick fix,” the classic vulnerabilities return.
Business Logic: Rare, but Serious When Found
Business logic issues appear less frequently, but when they do, the impact is typically significant. Examples include bypassing approval workflows, manipulating price calculations, or skipping required validation steps. These vulnerabilities do not show up in automated scanners and require a deeper understanding of how the application behaves.
Conclusion
The data confirms what many security professionals already know:
- Most vulnerabilities are avoidable with consistent configuration baselines and hardened deployments.
- Critical findings concentrate in authorization logic, not in exotic attacks.
- Legacy bugs persist whenever shortcuts or rushed deployments bypass the protections provided by frameworks.
If you build or maintain web applications, focus on secure defaults, structured API authorization, and proper session handling. These fundamentals prevent the majority of real-world issues.
